Managing the HR and compliance issues of social networking
Ted Ritter, Nemertes Research — 15 February 2010Enterprise social networking tools heighten business collaboration, but they also introduce new risks and challenges. In the absence of an aggressive, risk-based approach to HR and compliance regulations, business social networking tools – whether private or public – could put your enterprise in jeopardy.
You’ve just arrived in San Diego for a business trip. While heading to the hotel, you update your MyLinkedBook status page to announce your arrival. Pretty innocuous, right? Well, it turns out that one of your followers is a TechTarget reporter who suspects you’re involved in M&A activity, and this seemingly innocent update has just fueled the rumor that your company is buying Spaceley Sprockets out of San Diego. Welcome to the world of social networking! It is the next wave of enterprise online collaboration, and the best way for HR and compliance to get out in front of the wave is with a risk-based approach.
Enterprise social networking adoption
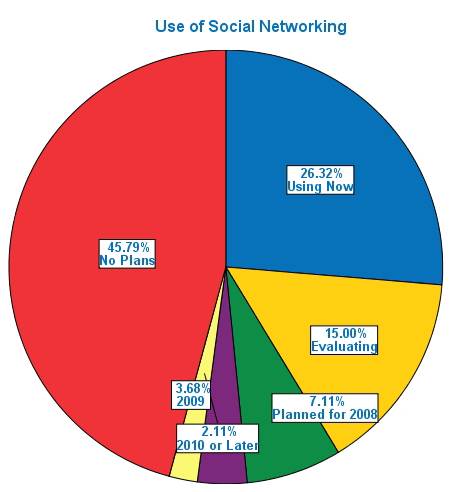
Social networking has seen rapid adoption by the general public, with enterprise social networking following. Participants in Nemertes’ research note a 26.32% adoption rate, with 45.79% indicating no intention to use. (Please see Figure 1: Use of Social Networking.)
Figure 1: Use of Social Networking
Businesses identify at least five major uses of enterprise social networking, including: creating brand awareness; online reputation management; recruitment; competitive analysis; and lead generation. The concern is that the use of business social networking is occurring ahead of best practices for human resources, compliance and legal functions. The opening example is just one case where an employee’s use of social networking jeopardized the business without the employee’s or management’s knowledge.
Guidance is just now starting to develop. Most recently, the Financial Industry Regulatory Authority (FINRA) issued social networking guidance, raising social networking to the same level of sensitivity as email and instant messaging. Though not prescriptive, FINRA guidance characterizes a risk-based approach to social networking.
FINRA doesn’t differentiate between use of a public social networking site like Facebook and a business social networking application like Jive. Take note: Employees will continue to use public social networking sites even when a business-class social networking application is available.
A risk-based approach to social networking
So, what can HR and compliance do to best prepare for online social networking? Here are five areas of focus:
- Take ownership
It’s time for a reality check. Those responsible for IT, HR, legal and compliance must get out in front of social networking. Simply blocking access to social networking sites doesn’t work because employees will find ways around the blocks. Establish an investigative committee to identify the potential benefits and risks of social networking for the corporation. The outcome of this analysis will determine the next steps.
- Engage compliance early
Compliance juggles a range of legislative, industry regulations and e-discovery requests on a daily basis. Particularly challenging is e-discovery, since social networking interaction falls under the category of electronically stored information (ESI), meaning that it’s discoverable and may be part of a legal action. There needs to be a way to record and monitor social networking interaction (see below). The compliance and legal personnel have the best insight into the reality of complying with these requirements for the corporation. Engage them early.
- Formal education program
Education is probably the best means to prepare for judcious use of social networking. Per the example at the opening of this article, had there been proper education, the employee would not have updated his status. In fact, with proper understanding, he might have updated the status to indicate that he was in San Francisco rather than San Diego, thus throwing off the snooping journalist — intentionally using social networking to competitive advantage.
- Strong password management
All social networking applications (public and private) use a password as the primary authentication mechanism. A weak password opens the door to someone else gaining access to a user account, and compromising a user password on a social networking site can open the door to corporate assets. This is exactly how Twitter was hacked. A Twitter employee used the same weak password on a Gmail account as on the Twitter corporate account. The bottom line is that employees must use strong passwords and different passwords for their public and private social networking sites.
- Monitor social networking activity
Social networking will go the way of instant messaging (IM). Initially, most organizations considered IM ephemeral and irrelevant to business functions. Changing attitudes have enterprises monitoring and archiving instant messaging just as they do email. Enterprises’ social networking applications such as Jive and Socialtext offer tracking features. A third-party application like FaceTime tracks both enterprise and public social networking usage.
By following a risk-based approach, those responsible for HR and compliance can get out in front of the enterprise social networking trend. It’s far better to be ahead of the wave than to wait till employees misunderstand and misuse social networking and its potentially harmful effect on the corporation.
About the author:
Ted Ritter is a senior research analyst with Nemertes Research, where he conducts research, advises clients, and delivers strategic seminars. A Certified Information Systems Security Professional (CISSP), Mr. Ritter leads Nemertes’ research on information stewardship, which includes compliance and the management, access, storage and backup of data.